How Bitcoin Solved The Byzantine Generals' Problem
Issue 103
✌️ Welcome to the latest issue of The Informationist, the newsletter that makes you smarter in just a few minutes each week.
🙌 The Informationist takes one current event or complicated concept and simplifies it for you in bullet points and easy to understand text.
🫶 If this email was forwarded to you, then you have awesome friends, click below to join!
👉 And you can always check out the archives to read more of The Informationist.
Today's Bullets:
The Byzantine General and His Problem
Real World Byzantine: Computer Networks
Bitcoin: Solving The Double Spend
Inspirational Tweet:
Periodically, you may hear, or have heard, the argument that Bitcoin solves the Byzantine Generals' Problem, and this is what make Bitcoin so unique, so valuable.
But who are these Byzantine Generals, and what's their problem?
And more importantly, why should we care?
Great questions, and perhaps more important than you may think. And though the Byzantine General concept may sound intimidating or even daunting, have no fear. Because we are going to unpack the idea nice and easy, as always, here today.
So, grab your favorite cup of coffee and settle in as we simplify some history and technology with The Informationist.
🤥 The Byzantine General and His Problem
First things first, the term Byzantine Generals' Problem originates from a paper published in 1982 by Leslie Lamport, Robert Shostak, and Marshall Pease.
See, the Byzantine Empire, also known as the Eastern Roman Empire, was founded when Constantine the Great relocated the Roman capital to Byzantium (modern-day Istanbul) in 330 AD. The Byzantine Empire stayed in power until 1453 AD, but experienced plenty of wars, religious conflicts, and political changes over the centuries.
So Byzantine is a fitting reference for the Byzantine General concept, as you will see.
Even though the empire and its wars were real, the problem and its name are metaphorical. It was designed, rather, to show the challenge of achieving reliable consensus in a distributed system.
The authors chose the Byzantine Empire's military command as a metaphor because of its historical reputation for complexity and intrigue, including problems of loyalty and communication.
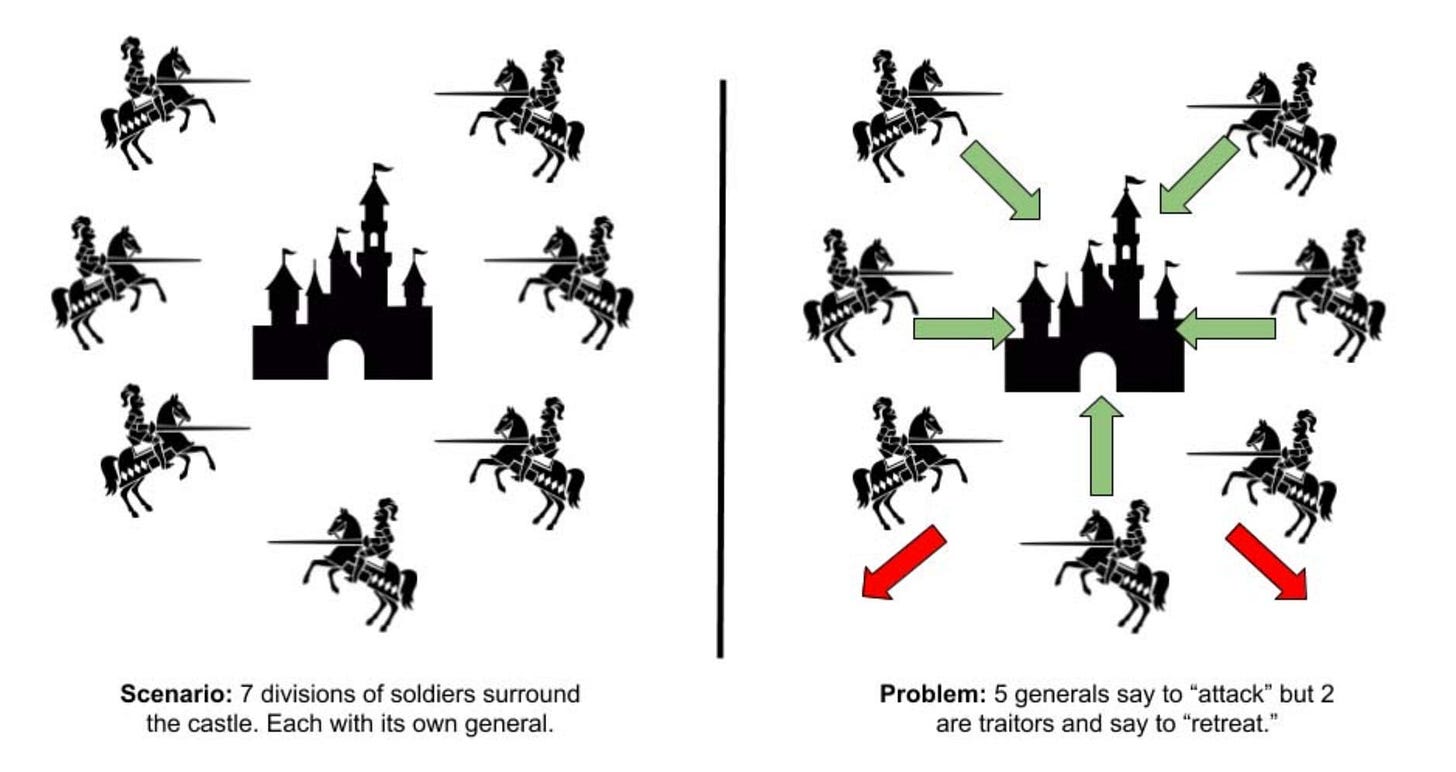
In the Byzantine Generals' Problem, several divisions of the Byzantine army are camped around an enemy city, and they need to agree on a common plan of action.
Being camped around the city, the generals can only communicate through messengers, complicating their ability to achieve consensus.
Worst of all, some generals might be traitors, trying to prevent the loyal generals from reaching any agreement.
These generals may send false messages or contradict the plans of loyal generals.
Problem is, for the attack to be successful, all loyal generals must agree on the same plan. And so, the loyal generals must find a strategy that guarantees agreement, despite interference or traitors.
The core of the Byzantine Generals' Problem is to design a system that ensures all loyal generals reach agreement on their plan, even in the presence of disinformation spread by traitors.
OK, so that's all well and good, but how does it relate to computers and, specifically, Bitcoin?
Let's dive a little deeper.
🤨 Real World Byzantine: Computer Networks
As you know, the Internet is essentially a massive, sprawling network of millions and millions of computers and devices, all connected and communicating with each other.
But, as each and every one of us has experienced, issues related to trust, coordination, and consensus often occur, due to faulty or malicious actors.
The Byzantine Generals' Problem is posed to understand these issues in distributed computer networks.
Let's look at a few:
Consensus
In distributed systems, like databases, cloud computing, and blockchain networks, nodes (computers keeping the records) must agree on the data (e.g., transaction history, database entries) despite the possibility of some nodes being unreliable or malicious.
For instance, a Sybil Attack, subverts the network by creating a large number of pseudonymous identities, using them to gain a disproportionately large influence.
Network Routing
Routing protocols rely on nodes to exchange information about the best paths for data packets to travel. Malicious or compromised nodes could suggest false routing information, leading to disruptions.
Here, attacks like BGP (Border Gateway Protocol) hijacking can occur, where an attacker misleads the network about the best path, potentially intercepting or blocking traffic.
Peer-to-Peer Networks
Peer-to-peer (P2P) networks, used in file sharing, cryptocurrencies, and certain types of web content distribution, must ensure that peers can trust the data they receive, despite the network's open and decentralized nature.
Eclipse Attacks target a node's view of the network, isolating it from honest peers and surrounding it with attacker-controlled nodes, thereby controlling the victim's access to information.
Authentication and Authorization
Ensuring that users or entities are who they claim to be, and that they can only access what they are allowed to see. Malicious actors could impersonate legitimate users or manipulate systems to gain unauthorized access.
Man-in-the-Middle attacks (MITM), where an attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other.
And that's just to name a few of the most important and prevalent challenges.
In order to address them (and others) a number of solutions have been developed.
Cryptography (literally the basis for crypto-currencies) helps hide data and identities,
And consensus algorithms, like Proof of Work (PoW) and Practical Byzantine Fault Tolerance (PBFT), help distributed systems agree on a single source of truth, even in the presence of malicious actors.
PBFT is essentially an algorithm that allows a certain number of faulty or malicious actors (Byzantine nodes), without affecting the network.
And then there is Bitcoin.
While many other cryptocurrencies attempt various protocols and algorithms like Proof of Work, none of them are fully distributed, except Bitcoin.
And so they are still susceptible to malicious actors or consensus breaches.
The problem essentially comes down to trust.
Or rather, not having to trust at all.
🤩 Bitcoin: Solving The Double Spend
For those of you who are new to Bitcoin, some important information.
Don't worry, we won't get too technical here.
First, Bitcoin's network of nodes (computers that talk to each other) is fully distributed, meaning there are tens of thousands of them across the world.
Each of these nodes keeps a full ledger (like an accounting record) of all transactions that have ever taken place on the Bitcoin blockchain. And this gets updated and verified roughly every ten minutes.
24/7.
The blockchain, also known as a timechain, is basically a long database that has all transactions timestamped, one after another, and like the mind of a two-year old toddler, it simply can never be changed.
How?
All the nodes keep each other in check by confirming that the blockchain any node proposes does in fact match all the other nodes' blockchain records.
A fully distributed ledger.
In other words, all the other nodes must agree with the timestamped record of transactions. If a node does not agree, it is effectively removed from the network.
And this solves The Double Spend Problem.
I.e., if a node attempts to approve a transaction that would allow a Bitcoin to be spent more than once, the transaction is rejected (by all the other nodes), and the malicious or bad acting node is simply ejected from the network.
Booted like a rat from a cheese factory, it will be ignored by or disconnected from other nodes. Isolated and all alone.
Rejected.
From Satoshi's White Paper itself:
The steps to run the network are as follows:
New transactions are broadcast to all nodes.
Each node collects new transactions into a block.
Each node works on finding a difficult proof-of-work for its block.
When a node finds a proof-of-work, it broadcasts the block to all nodes.
Nodes accept the block only if all transactions in it are valid and not already spent
Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash.
So, in order to have a true permissionless and trustless network it must be distributed (fully decentralized).
Centralization of decisions or authority leaves too much power in the hands of one or a few actors who could be malicious or have ill intent.
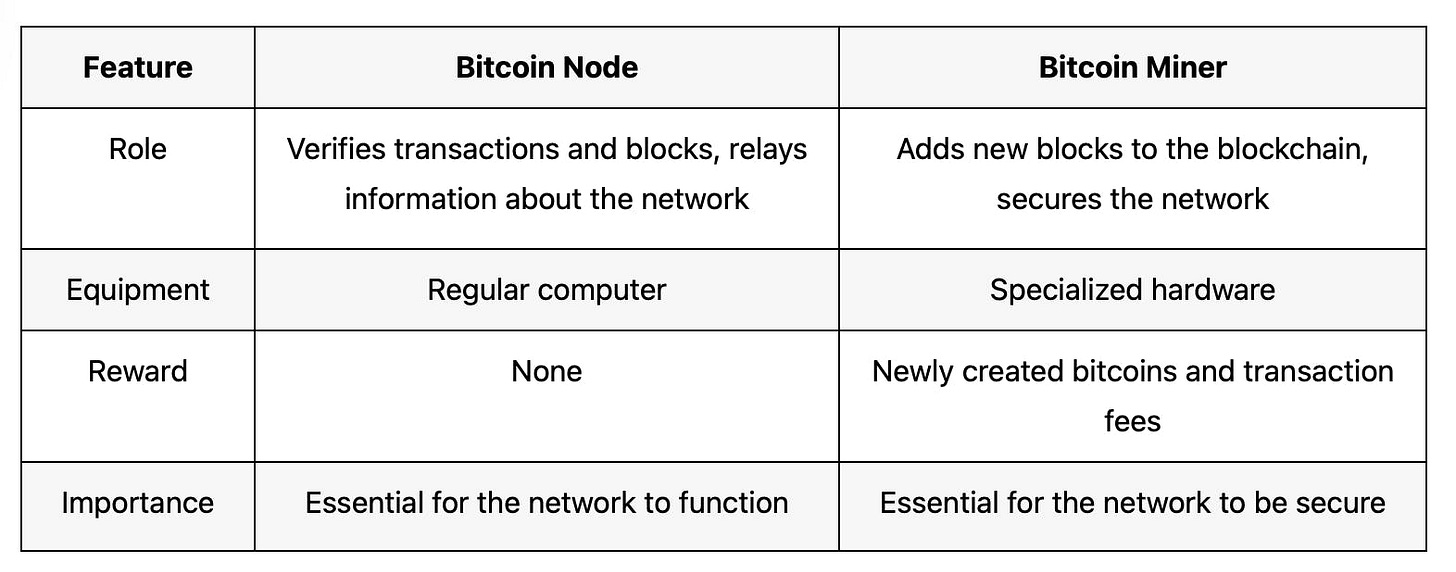
One note here: all Bitcoin miners are nodes, but not all nodes are miners.
In other words, the miners are performing the Proof of Work, keeping the network secure by performing computations that require (now massive) amounts of energy in order to mine Bitcoin.
Miners must solve a computationally difficult puzzle to add a new block to the blockchain (Proof of Work). This ensures that creating blocks is expensive and requires significant computational resources. This protects the network against spam and malicious attacks, as altering the blockchain would require an impractical amount of computational power.
As for the non-miner nodes, they're more like librarians or gatekeepers.
And this is how Satoshi and Bitcoin's growth as a fully distributed and massive computationally powered network has become a novel solution to the Byzantine Generals' Problem.
Instead of a central authority approving the transaction, the entire network must approve it.
This removes the need for trust.
You don't have to know who you are buying or selling your Bitcoin to.
You don't have to know or trust a third-party facilitator (like an eBay or an Etsy) to assure trust between parties (i.e., send money, receive goods).
You don't have to know or trust a third-party custodian (like a Lehman Brothers or Bear Stearns selling you a derivative).
You just have to trust the network as a whole, like a massive community that has perfectly aligned incentives to see that your transaction is settled properly and a record of it is kept on the Bitcoin blockchain (timechain) forever.
And that, my friends, is one of the core aspect of Bitcoin that makes it so very valuable.
In fact.
Irreplaceable.
That’s it. I hope you feel a little bit smarter knowing about The Byzantine Generals' Problem and how Bitcoin has solved this for distributed networks.
If you enjoyed this newsletter and found it helpful, please share it with someone who you think will love it, too!
Talk soon,
James✌️